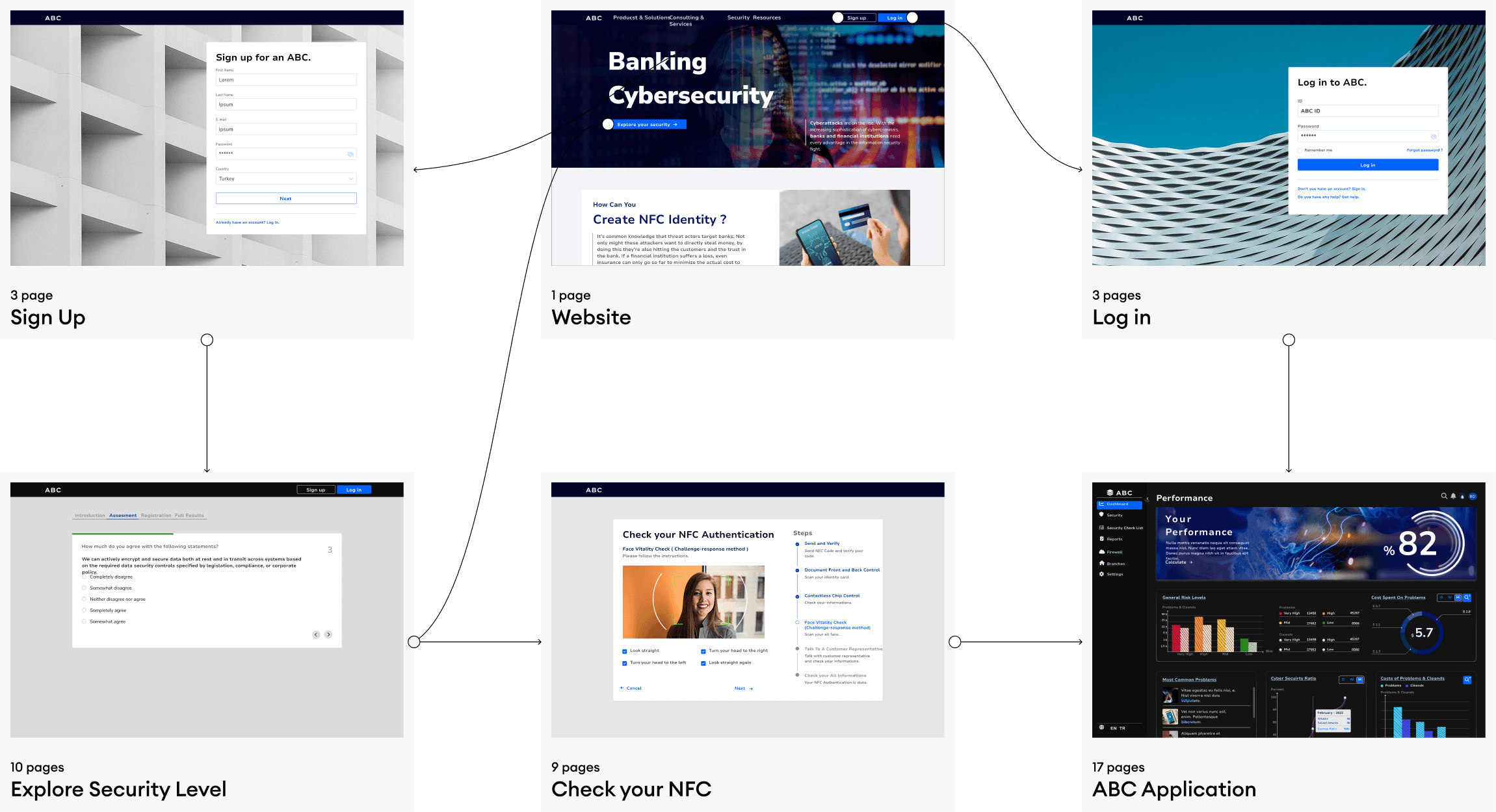
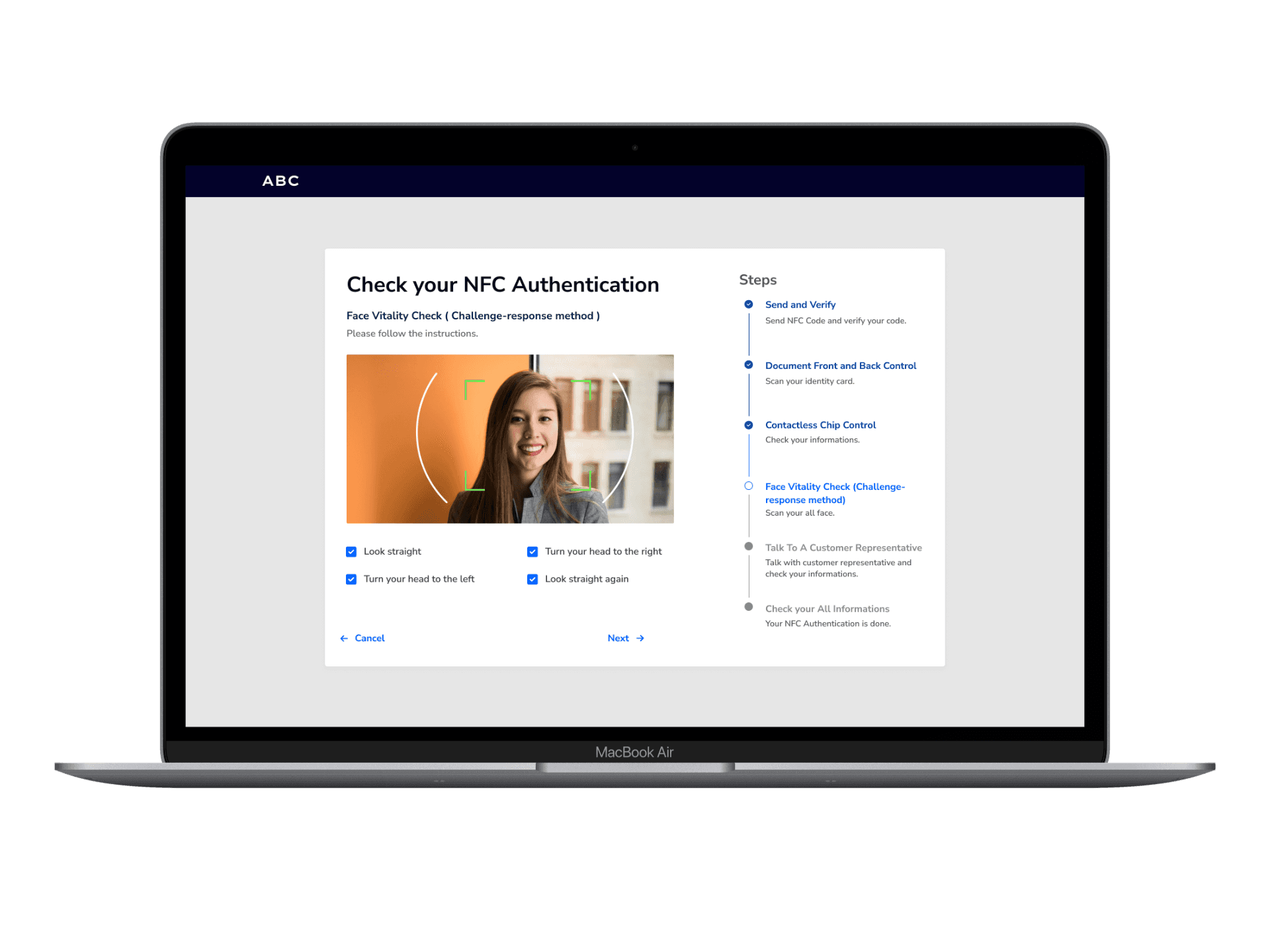
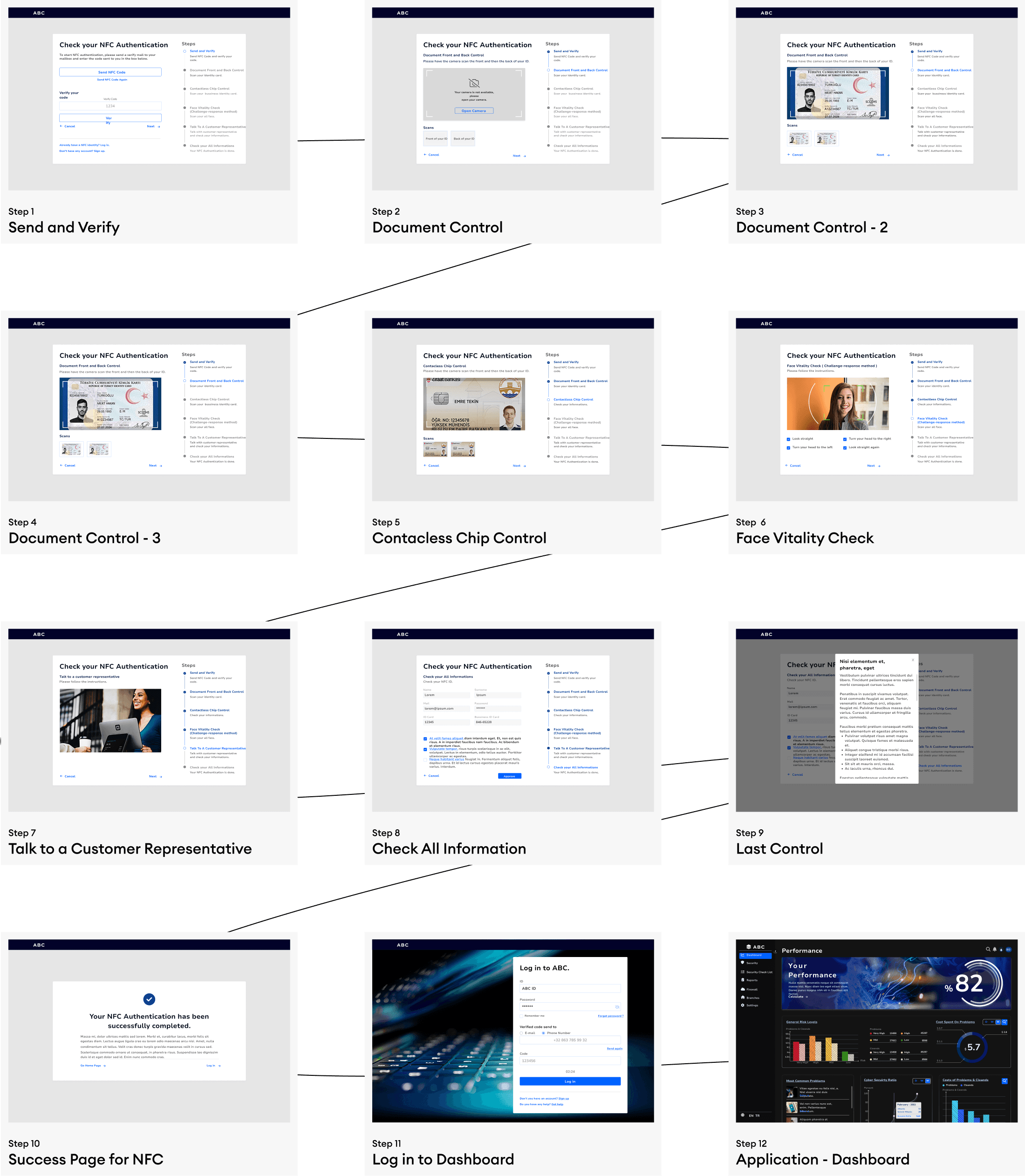
Cybersecurity Management for Banks and Branches
ABC is a desktop app that verifies how prepared banks are against 'cybersecurity threats.'
Introduction
**Enhancing Cybersecurity for Banks: A UX Case Study** With rising cyber threats in the financial sector, banks need robust solutions to assess and strengthen their security. This cybersecurity application enables banks and branches to **monitor systems, detect vulnerabilities, and take proactive measures** through interactive reporting, security scans, and risk analysis. In this case study, I will outline my **UX design process from low to high fidelity**, focusing on intuitive workflows, data visualization, and user-centric solutions that drive effective decision-making.
Role
Mid. Level UX / UI Designer
Industry
EdTech
Year
2022
Duration
2 Weeks
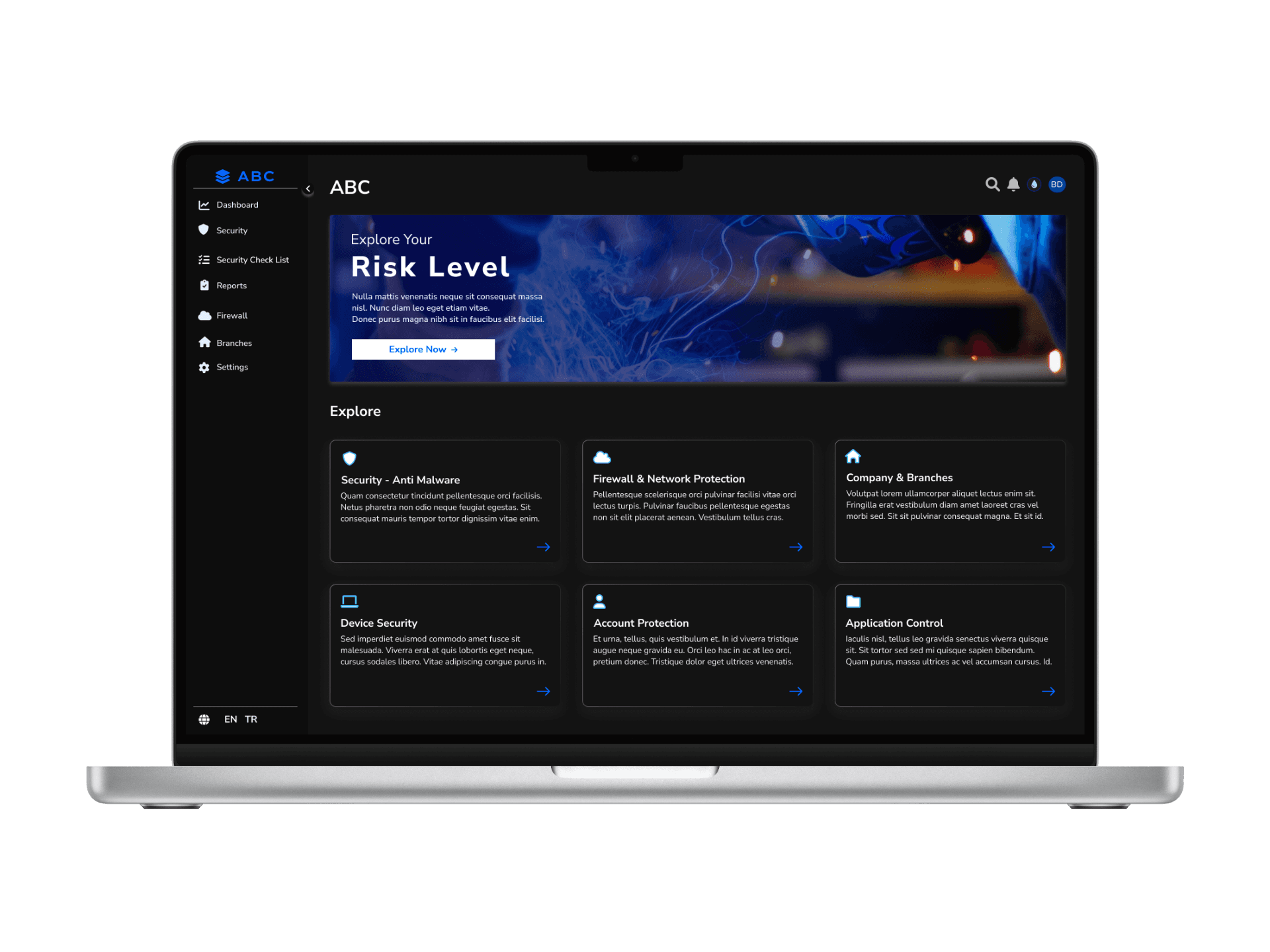
Solution - 3 // Application - Home Page
I designed the general screen that users encounter after successfully completing their registration to help them learn how to use the platform's features by classifying the available options. Since it is a detailed platform that could grow with evolving needs, I chose to use a menu to prevent users from always returning to the home page.
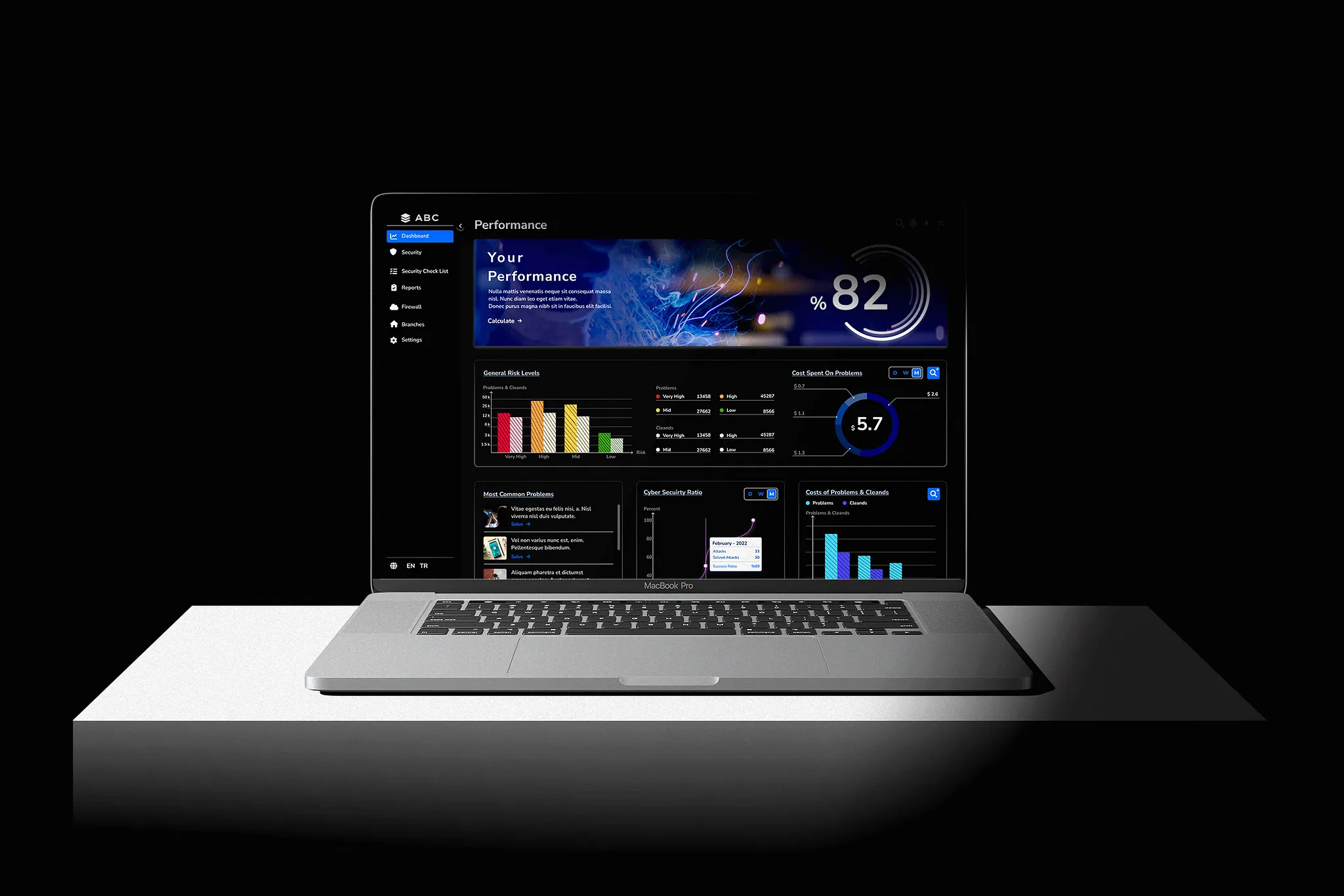
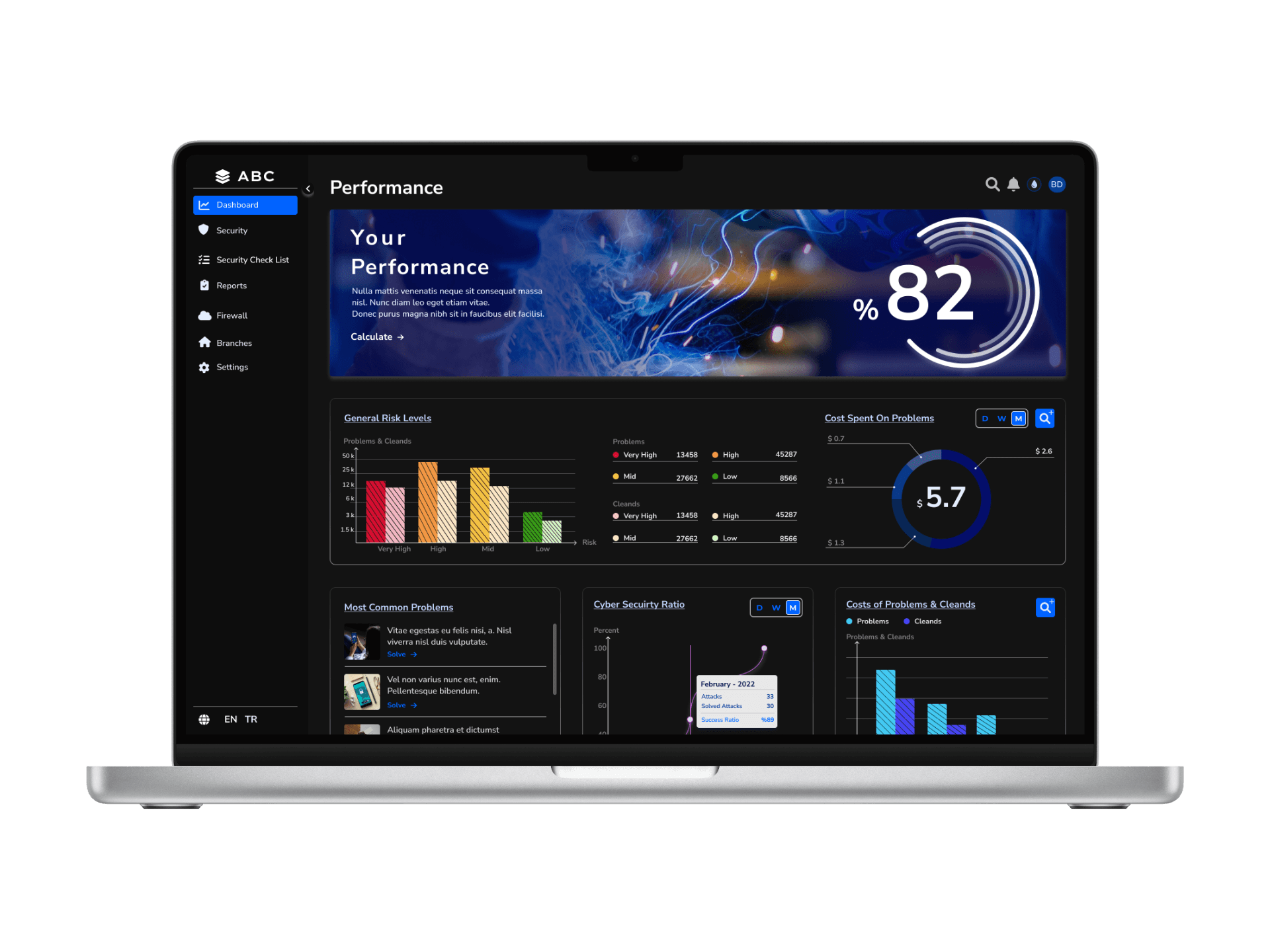
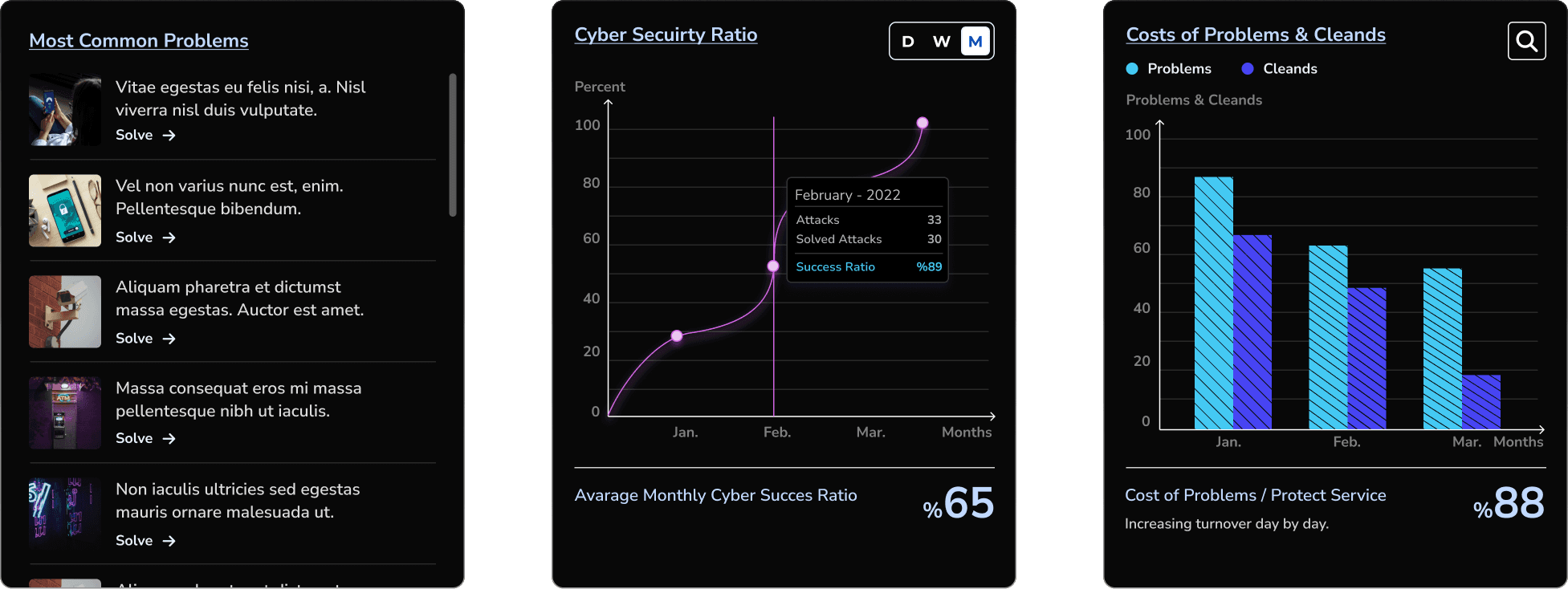
Solution - 4 // Application - Dashboard
For users who have uploaded their data, I aimed to create user flows using various statistical displays for features they might always want to know. Although the overall design of the dashboards uses a monochromatic color scheme, I chose semantic colors for displaying material-scale damage. I used line chart bars to enhance readability.
Solution - 6 // Application - Security Check List
I designed a checklist that allows users to easily filter the data they have uploaded and take action on the selected issues. This structure enables problems to be listed in a non-historical order. Additionally, by going to the Problem Details page, users can track how frequently the same error recurs. Each audit results in 15,000 – 30,000 reported issues, making data visualization, filtering, and prioritization essential for usability.
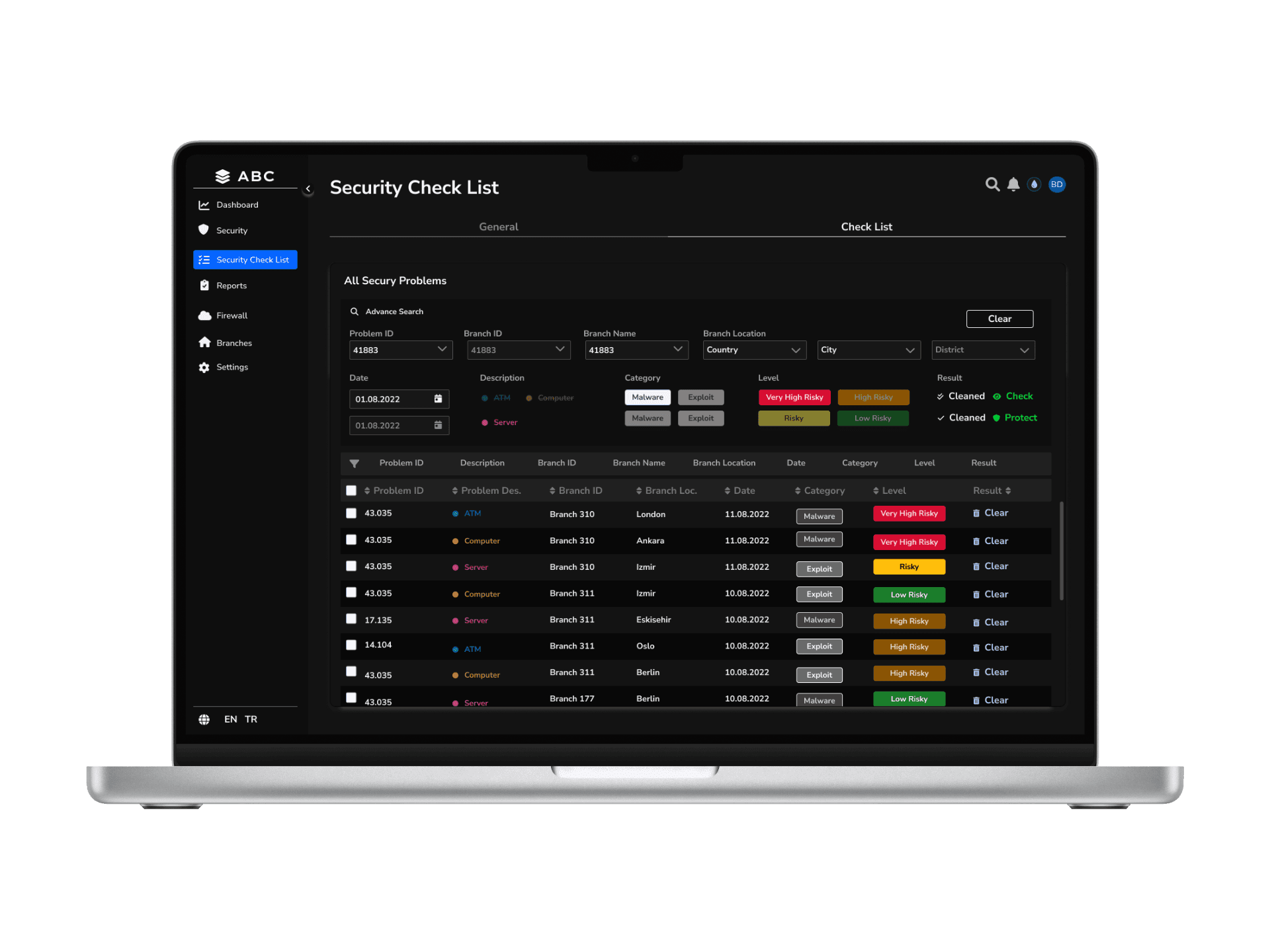
Issue Prioritization Mechanism
Severity Filters: Small, Medium, Major, and Critical issues can be filtered.
Regional Segmentation: Differentiates security risks between the central bank and branches.
Responsibility-Based Sorting: Separates actions needed by central management from those required at branch level.
Color Coding
Green, Yellow, Orange, and Red represent different risk levels.
Critical threats in red, minor issues in yellow or blue for clear prioritization.
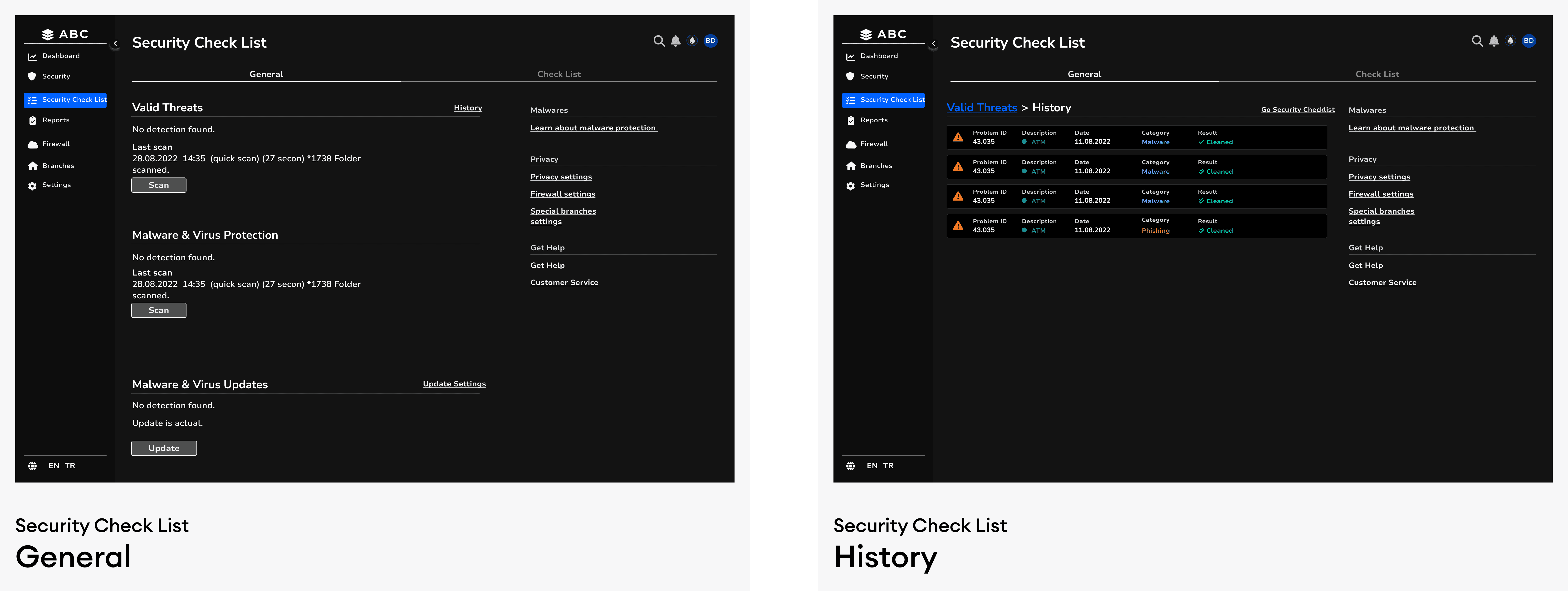
Hierarchy of Information
High-level summaries are displayed using large, prominent cards, while detailed insights are accessible through collapsible sections and tabs.
Users can always return to the Summary View with a dedicated button.
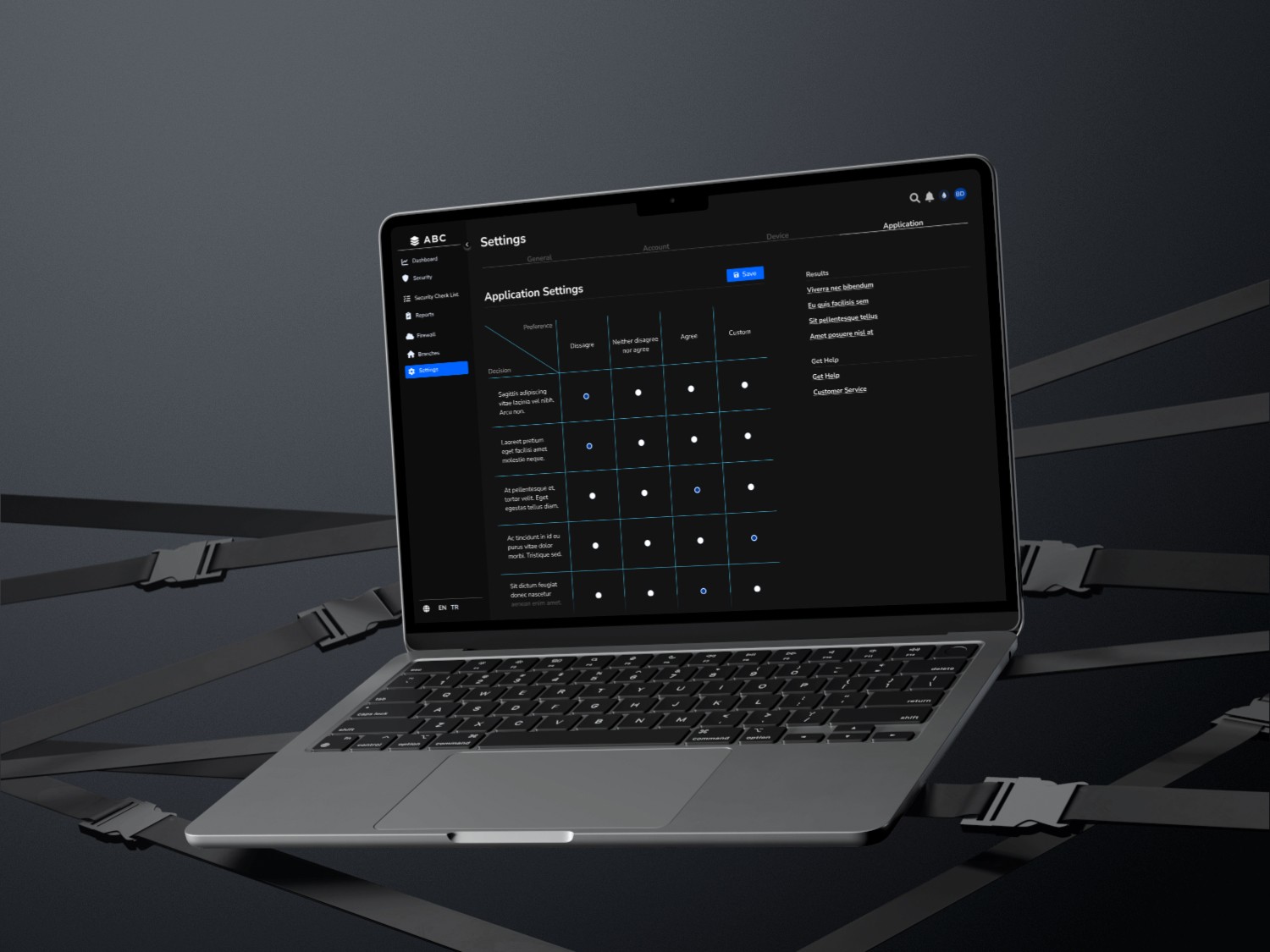
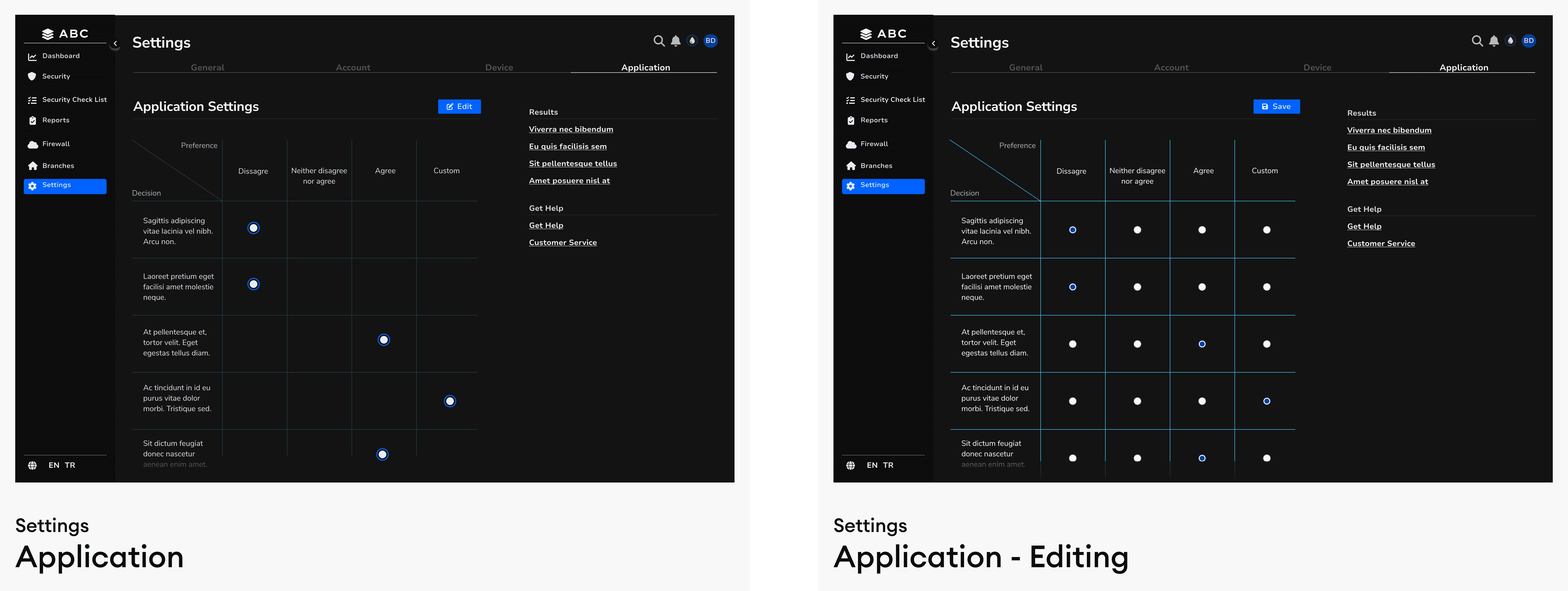
Solution - 6 // Application - Settings
I designed a structured Settings menu to enhance usability and organization, dividing it into General, Account, Device, and Application sections. The Account section not only manages user profiles but also enables branch-level security monitoring, allowing administrators to oversee and control branch activities seamlessly.
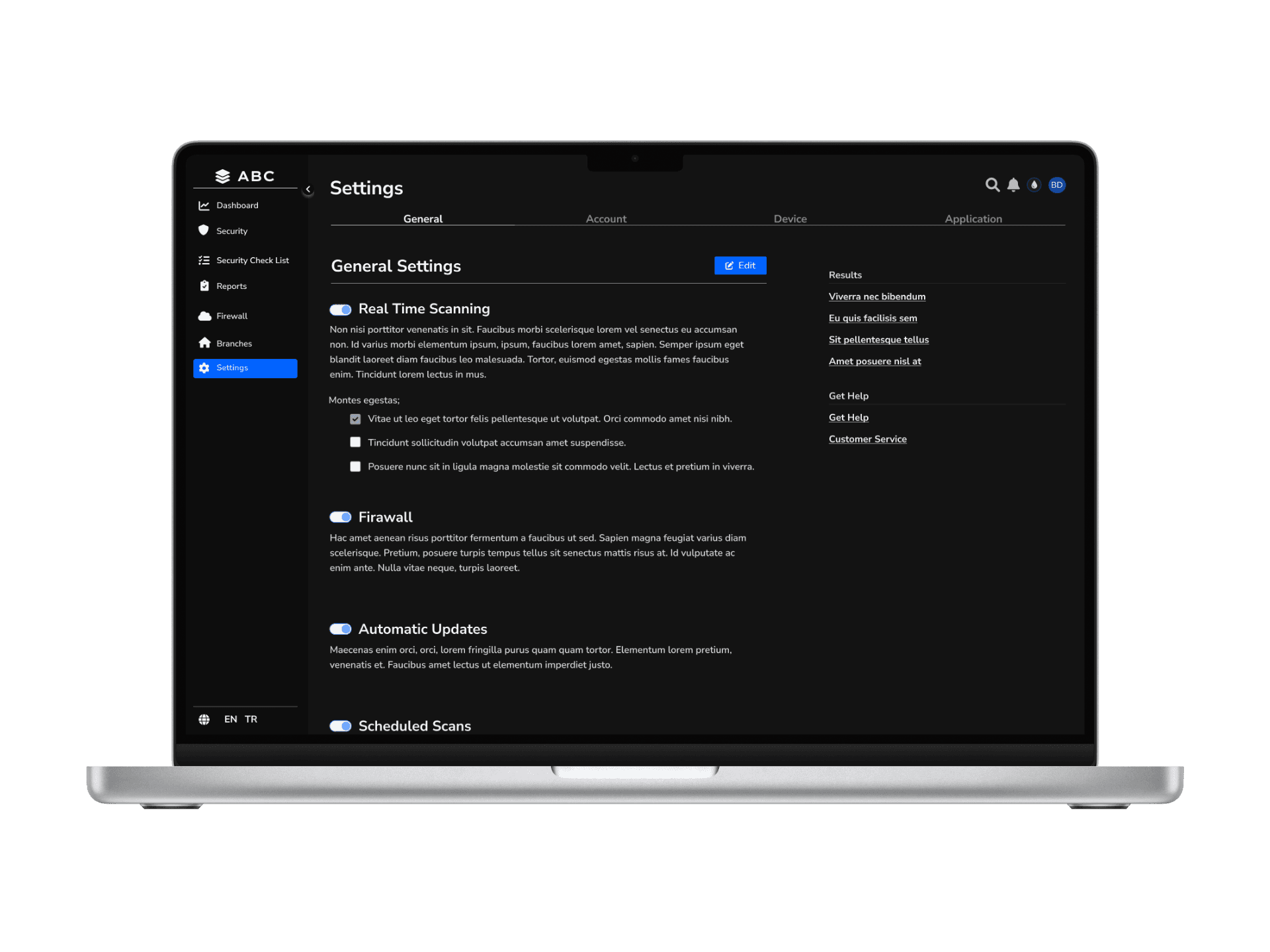
To ensure the most effective approach, I researched existing antivirus scanning applications and integrated industry best practices. My findings confirmed that this structured methodology aligns best with the case requirements, optimizing security management, usability, and scalability within the banking ecosystem.
Solution - 7 // Application - Security Scanner
To enhance cybersecurity monitoring and risk management, the Security Scanner plays a crucial role in providing real-time protection insights. This tool not only visualizes the bank’s current security status but also offers customized scanning options to detect vulnerabilities at different levels. By integrating historical risk trends and instant scan feedback, the Security Scanner enables executives to make data-driven decisions and take immediate action to strengthen their bank’s cybersecurity posture.
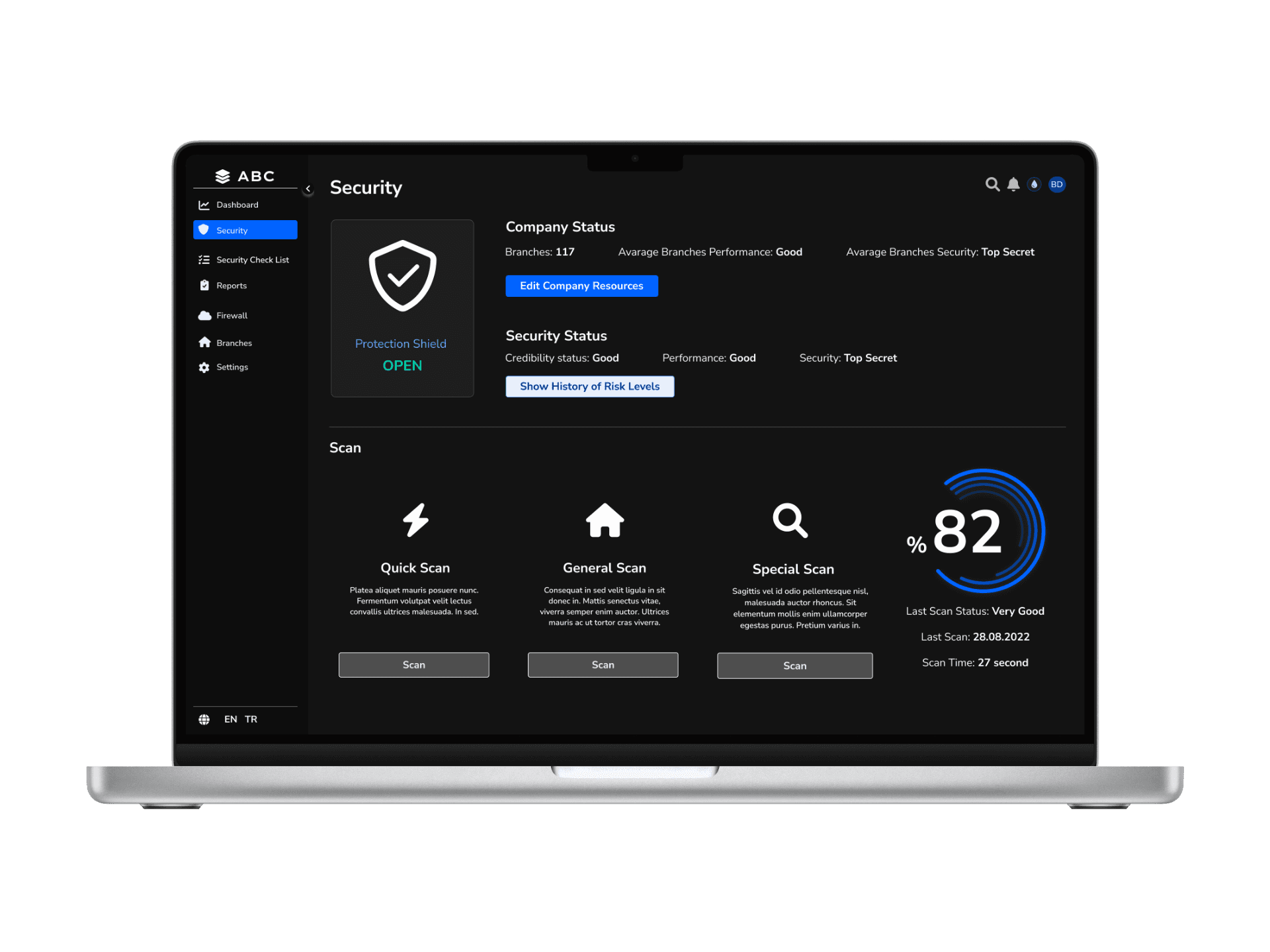
Security Scanner Section (Protection Shield UI)
A dynamic protection shield visualization updates based on the bank’s real-time security status.
Displays last scan results and the timestamp of the most recent scan.
Scanning Options
Quick Scan – Fast and high-level risk assessment.
General Scan – In-depth security scan across the entire banking system.
Branch-Specific Scan – Focused security checks for individual branches.
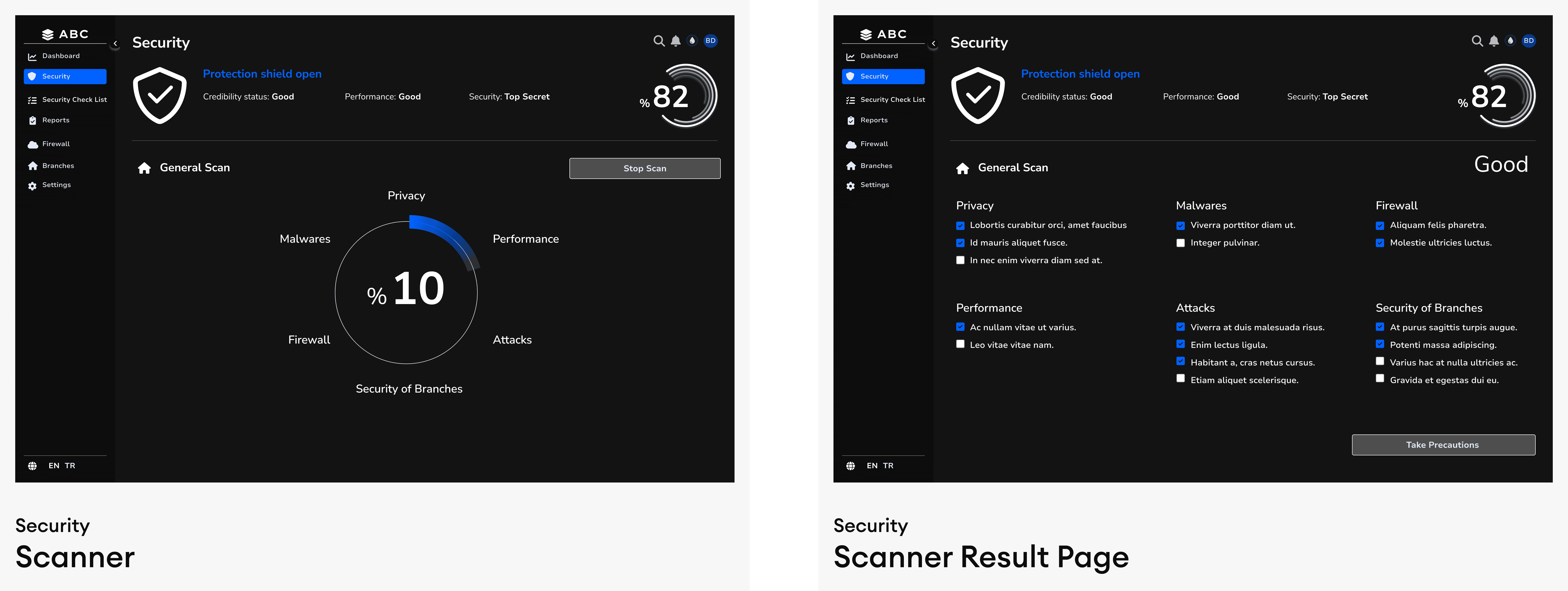
Scan History & Risk Trends
The “Show Risk History” section enables users to compare past and current security levels.
Trend indicators (e.g., graphs) display risk progression over time.
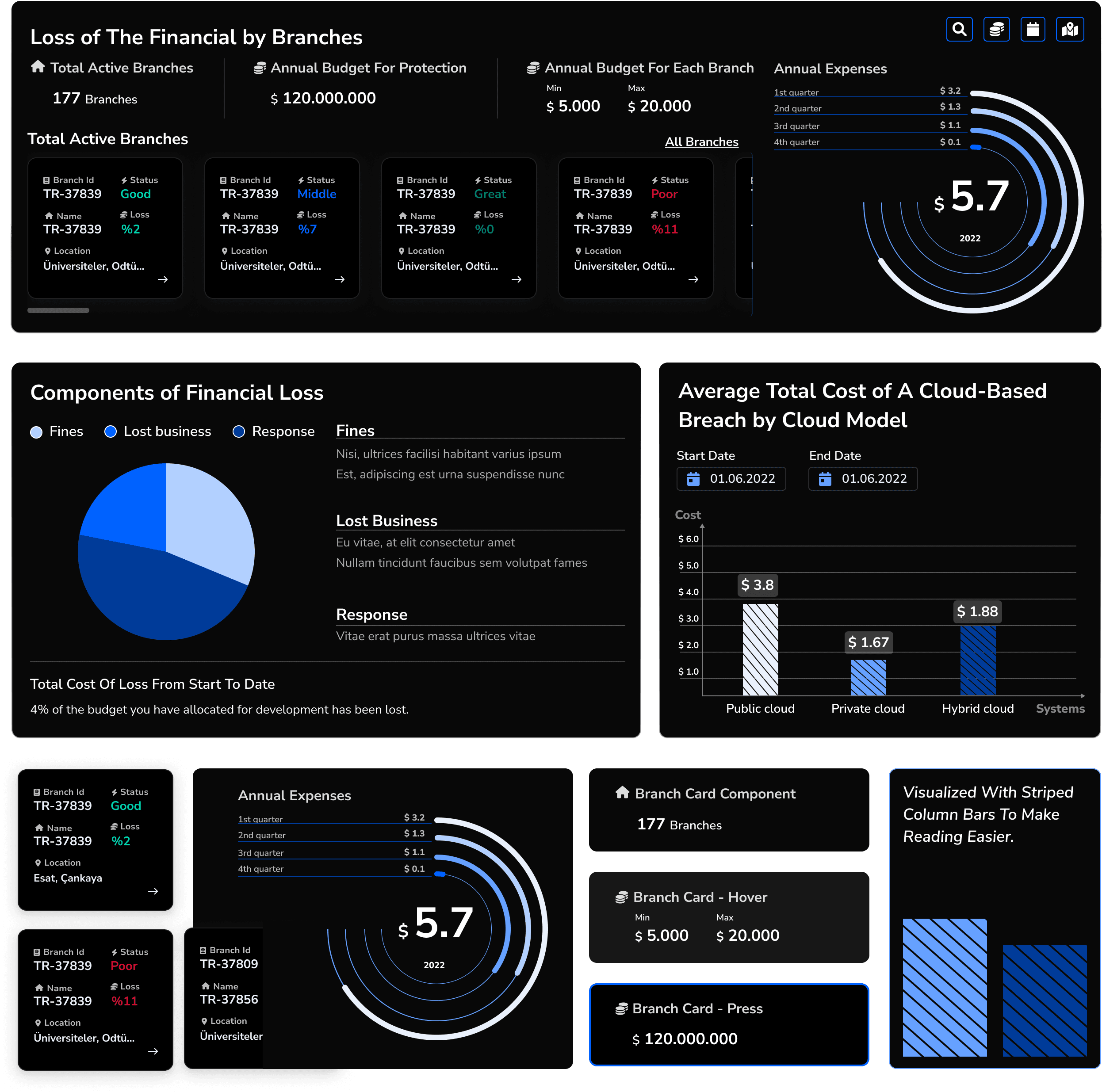
Solution - 8 // Application - General Reports Page
I designed the Report Page to display risk levels both at a general and branch-specific level, incorporating financial impact insights related to existing or potential security threats. From the main report dashboard, users can navigate to branch-specific or overall security details for deeper analysis.
To enhance visual clarity and data hierarchy, I utilized shades of the primary brand color, allowing semantic colors (red, green, blue, yellow) to stand out more effectively. Additionally, I implemented striped bar charts to improve data readability, ensuring a clearer and more structured representation of risk insights.
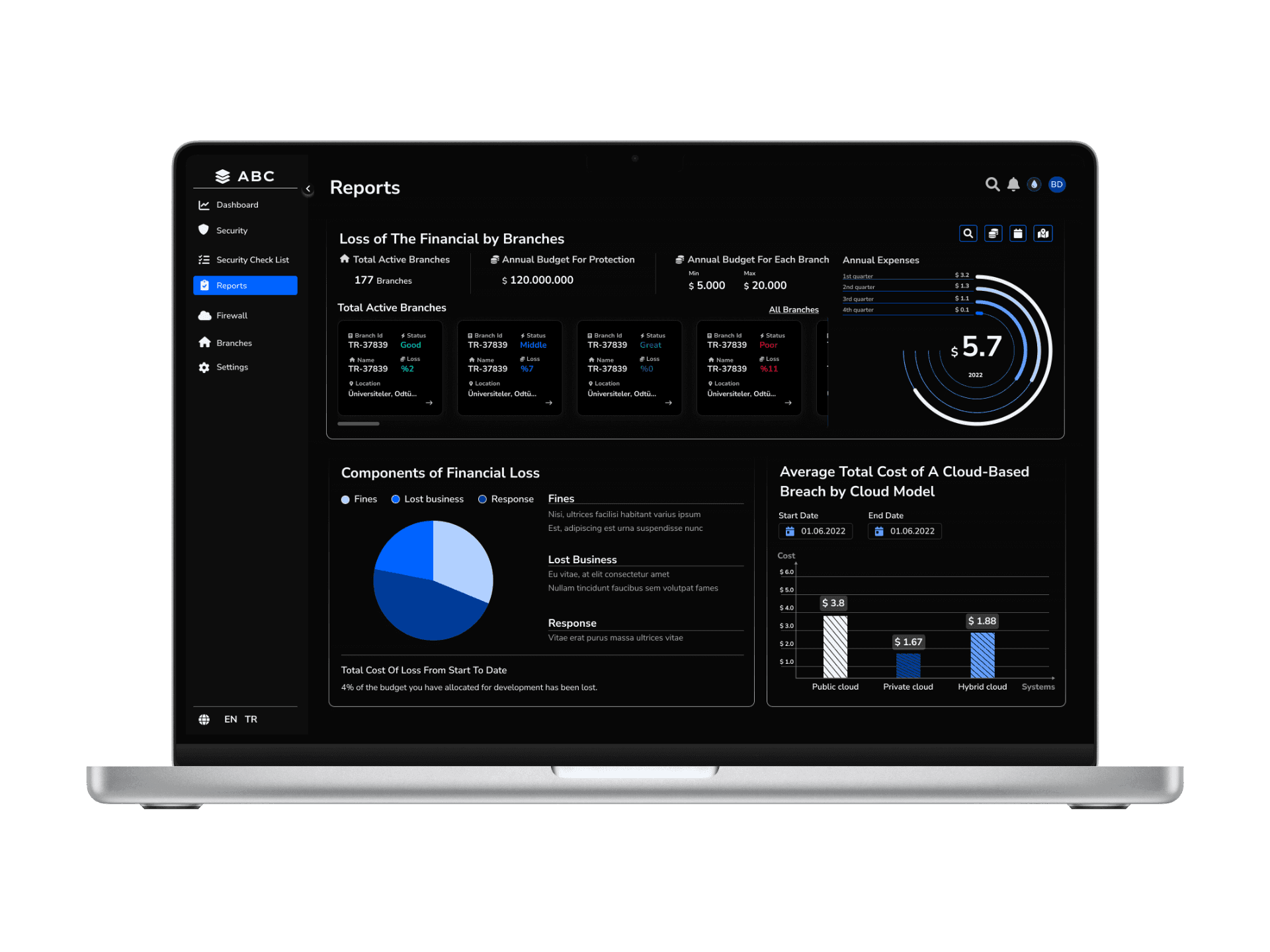
Overview Dashboard
A Security Score (e.g., 0-100) provides a quick assessment of the bank’s cybersecurity posture.
The most critical security risks are highlighted.
Threat categories (Good, Poor, Exploits, etc.) are visualized through graphs.
Detailed Report Page
Clicking “View Details” leads to an in-depth breakdown of security threats.
Regional Breakdown: A comparative view of security risks across different branches.
Actionable Steps & Recommendations
Central Management Strategies: Recommendations for overarching security policies.
Branch-Level Actions: A separate section outlines what branches can do independently.
Reflections
This UX design approach transforms complex cybersecurity data into an intuitive, actionable interface, allowing users to quickly grasp critical threats and take informed actions.
It reflects your expertise in managing data-heavy projects, analyzing user behaviors, and developing effective interaction models and design systems.
Other projects
MobileAction
Designing a Scalable Onboarding Experience for a Powerful ASO & Ad Management Platform.
Getir Oto / Design Case
Revolutionizing the educational ecosystem with a mobile app designed to enhance interactive learning and peer collaboration.
Fleet Management
Designing a desktop app to optimize fleet management and logistics coordination, from real F-16 pilot insight to prototype.
A Real Case Study: Smart Watch Application for Runners
As part of this design case, I am conducting interviews with runners to understand their needs, challenges, and motivations. By gathering insights from real users, I aim to create a solution that enhances their training experience, helps them track performance, and keeps them motivated.